Posted in : Microsoft, System Center, Windows Server By Johan Nilsson Translate with Google ⟶
5 years ago
Once more it was time to upgrade our SCCM environment to the newest release that is 1806. As it was not released for everyone yet, I had to run the Fast-Ring script to allow the update to present itself. I found this update very interesting as it comes with some exciting new features, and there are alot. These are the ones that I am most excited about.
- Ability to PXE boot without WDS
- CMTrace installed as default on clients
- Ability to exclude Active Directory containers from discovery
- High availability on Site Server
- CMPivot
- Boundary group for peer downloads
- Enhanced HTTP site system
- Improvements to OS deployment
- Software Updates for third-party
…and much more. You can read about all the new features here on Microsoft docs.
Since there are a lot of news, I have chosen to cover the two that I am most excited about in this new release.
CMPivot
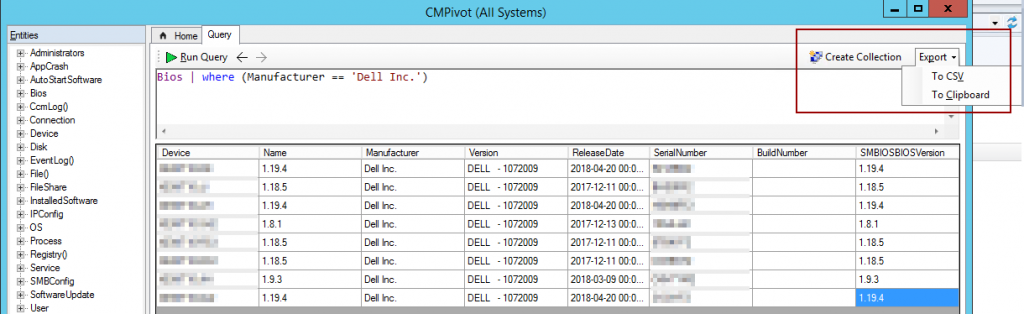
Configuration Manager is a very helpful tool when gathering information, CMPivot now allows you to take it to the next step by real-time querying clients. This allows you to gather a lot of information instantly. This feature uses Azure Analytics Language, .
CMPivot is located under Asset and Compliance > Overview > Device Collection, you can find this new feature in the top ribbon bar.
An example is to find BIOS-information about the Dell computers that are currently online. From this output you easily create a collection (the members of the collection will be added as Direct Members) or export to both CSV and Clipboard.
PXE Without WDS
It is exciting to have a new way of deploying over PXE. Since Windows Deployment Services has been available for a long time, it feel suitable to have an updated way of deploying clients. By replacing WDS, the distribution point will create the service ConfigMgr PXE Responder. If you have plans of using Multi-Cast, you are for now stuck with WDS.
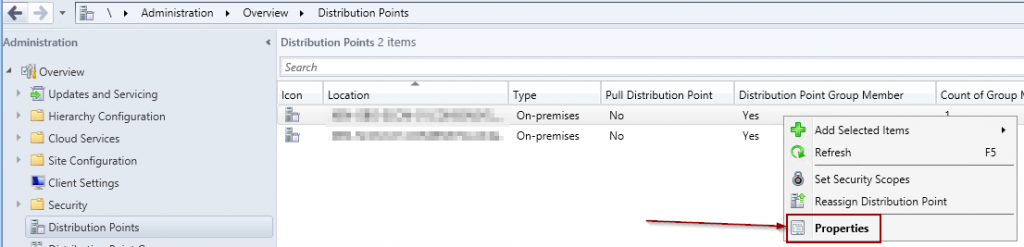
This setting can be found under Administration > Overview > Distribution Point, right click on the distribution point you would like to modify with the setting shown below.
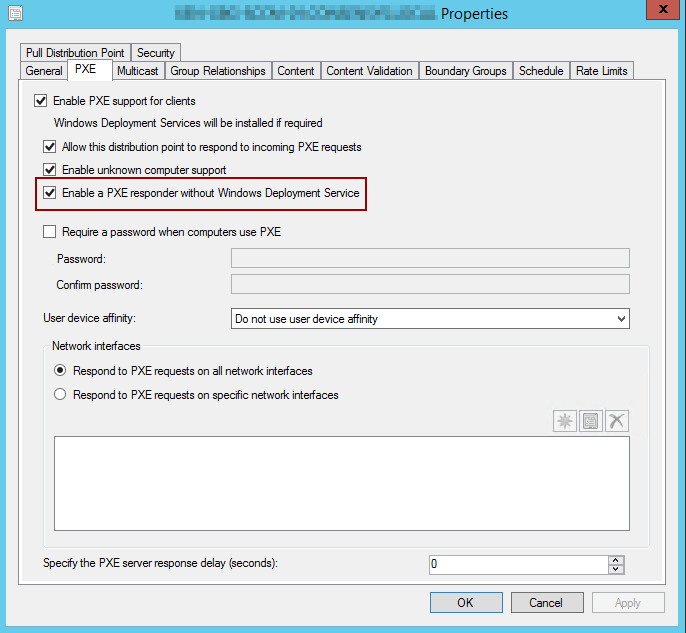
After applying this setting, Windows Deployment Services will automatically be disabled. Be advised that if you are monitoring this service, it will be report as stopped.

If you have questions, thoughts or anything you would like discuss? Send an email to Johan.Nilsson@xenit.se and I will be more than glad to talk about these topics.
Tags : 1806, CMPivot, ConfigMgr, Configuration Manager, PXE, SCCM, WDS
Personlig rådgivning
Vi erbjuder personlig rådgivning med författaren för 1400 SEK per timme. Anmäl ditt intresse i här så återkommer vi så snart vi kan.
Add comment